Mini Container Series Part 6
[This is the seventh article in this series. The previous one can be found here. Summary In the past few notes, with the help of Linux namespaces, we have limited what resources can be seen by a c...
[This is the seventh article in this series. The previous one can be found here. Summary In the past few notes, with the help of Linux namespaces, we have limited what resources can be seen by a c...
[This is the sixth article in this series. The previous one can be found here]. Summary Now, we are going to isolate network resources with the help of network namespaces, veth devices and Linux b...
[This is the fifth article in this series. The previous one is here]. Summary While doing process isolation, we isolated processes running inside the container from the rest of the host. However, ...
[This is the forth article in this series. The previous one is here]. Summary After the last two long articles, let’s take a break and discuss something simple. In this article, I will talk about ...
[This is the third article in this series. The previous one is here]. Summary Next, we are going to make the container think that it is the only process running in the system. This can be achieved...
[This is the second article in this series. The first one is here]. Summary For the first step, we are going to make the container think that it owns the entire filesystem. This can be achieved by...
Summary Recently, I learned some container technologies in Linux such as namespace and cgroup. However, after reading several articles and man pages, there was still one question lingering in my he...
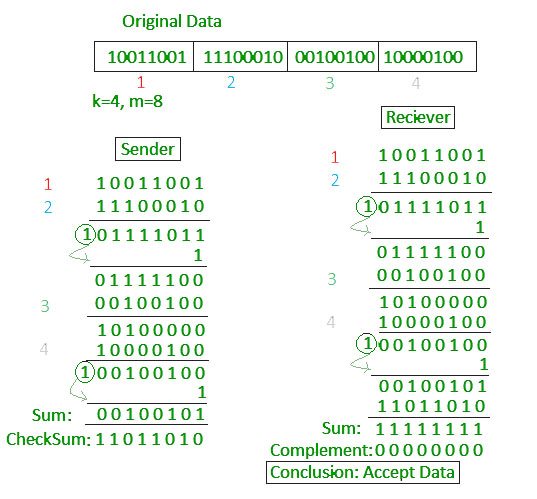
tl;dr If you don’t want to shoot yourself in the foot, then don’t mess up with checksum in any way. But if you’d like to see a counterexample, keep reading this note written by lame me. Background...
Summary Our project uses Identifier-Locator Addressing (ILA) for IPv6. Recently, we noticed that traceroute doesn’t work well for SIR address. The problem is, though traceroute can reach ILA router...
Tcpkill tcpkill is part of dsniff, a collection of tools for network auditing and penetration testing. It can be used to kill specified in-progress TCP connections. How does it work? The way tcpki...